Using on Fargate
Use Secrets Manager to interact with Fargate
You need to complete RDS Phase before you can continue below.
Overview
In this section, we will learn how to use the Secrets Manager service with AWS Fargate.
AWS Fargate is a compute engine used for Amazon ECS (Elastic Container Service) service that allows us to instantiate Containers without having to manage to compute or must configure the VMs. This is a step forward to help us reduce the load on deciding which EC2 Instance Type is suitable to run our application as well as making decisions about Scaling. At that time, we will focus more on designing and building the current application.
The CloudFormation Template used for this exercise prepared us with the shell scripts needed to build Docker Image and Amazon ECR (Elastic Container Registry). The exercise will focus on Secrets Manager rather than on Docker, Amazon ECS, or Amazon ECR.
Regarding the architectural model, the prepared AWS resources will be linked as follows:
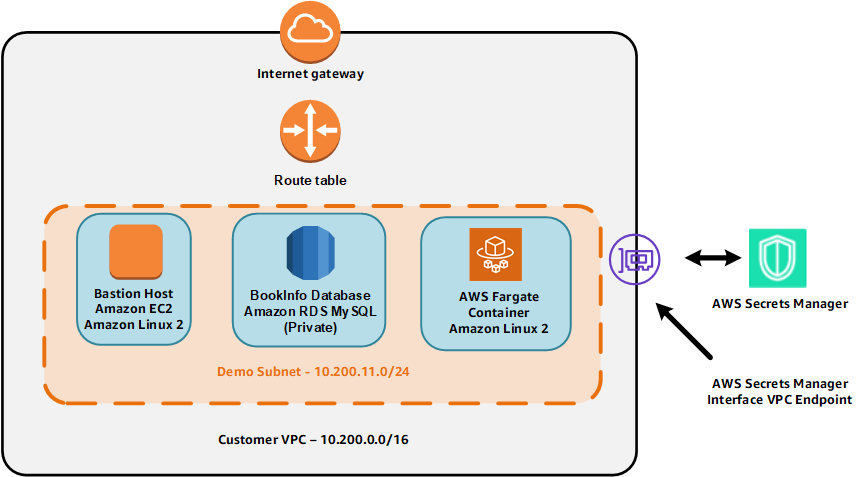
Contents
- Overview
- Prepare Docker Images for Amazon ECR
- Configure AWS Fargate
- Access to Fargate Containers
- Access to RDS Database
- Conclusion and a better understanding of the process
Prepare Docker Images for Amazon ECR
Access to Bastion Host with Session Manager
- Access the service Systems Manager
- In the left-hand navigation bar, select Session Manager.
- Press the
Start Sessionbutton. - Select the EC2 instance corresponding to the BastionIP value and press the
Start Sessionbutton.
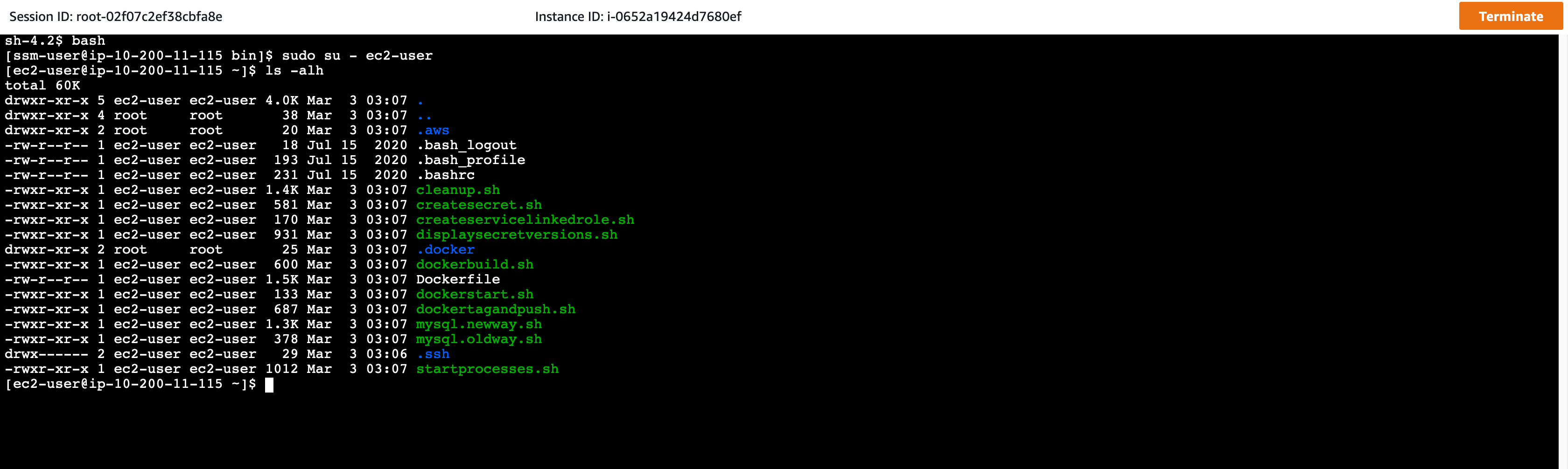
- In the new window bar, we will proceed to run the necessary commands.
Before running the scripts, we need to make sure the account used is ec2-user.
Proceed to switch to ec2-user account with the following command:
sudo su - ec2-user
Build Docker Image
We proceed to build Docker Image using the shell script dockerbuild.sh. This code will proceed to create Docker Image based on Dockerfile prepared (by CloudFormation).
./dockerbuild.sh
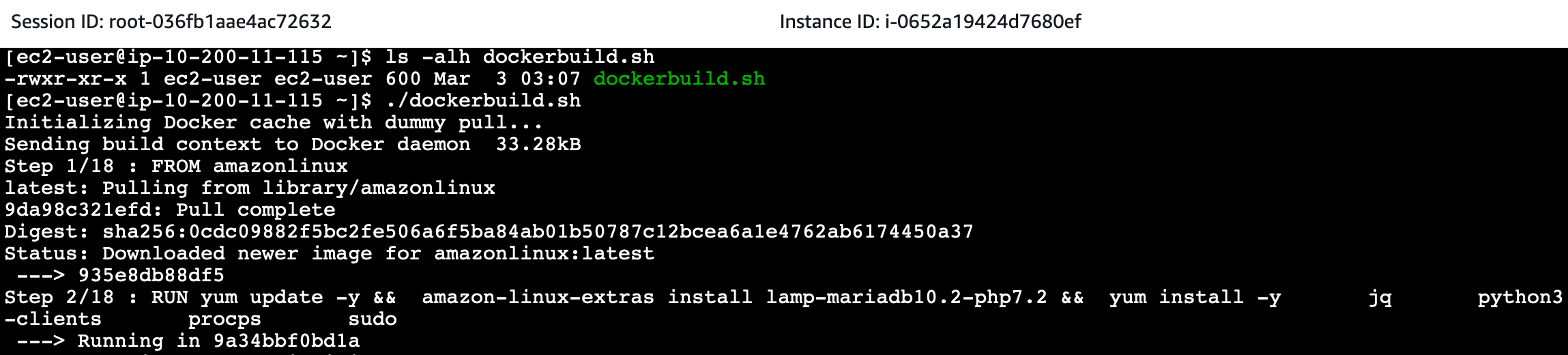
Building the Docker Image will take a few minutes to complete.
After the process is complete, we check the Docker Image named with -ecrre- format with the following command:
docker images
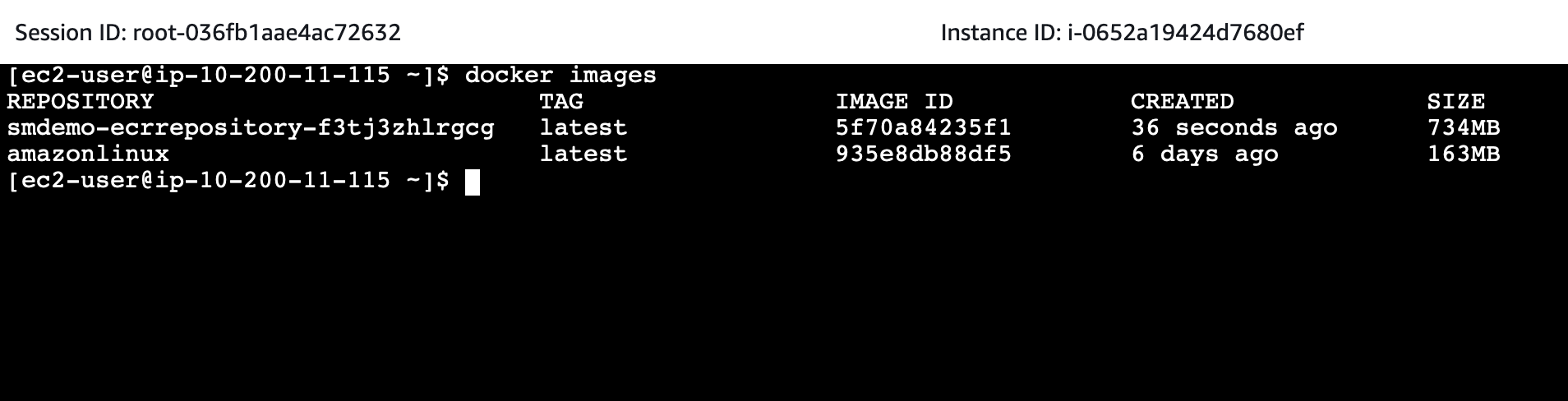
Once confirmed, we proceed to push this Docker Image to Amazon ECR using the shell script dockertagandpush.sh.
./dockertagandpush.sh
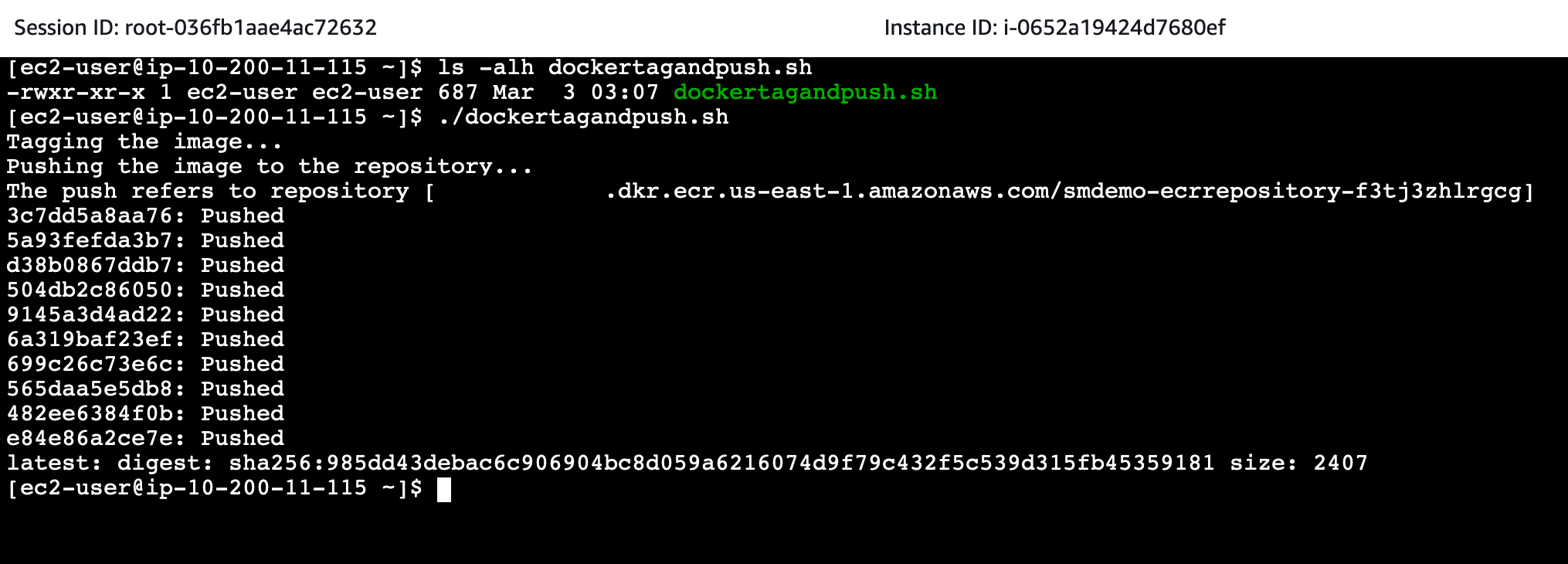
Pushing the Docker Image to Amazon ECR will take a few minutes to complete.
- Go to Amazon ECR
- Confirm that the latest Image has been uploaded.
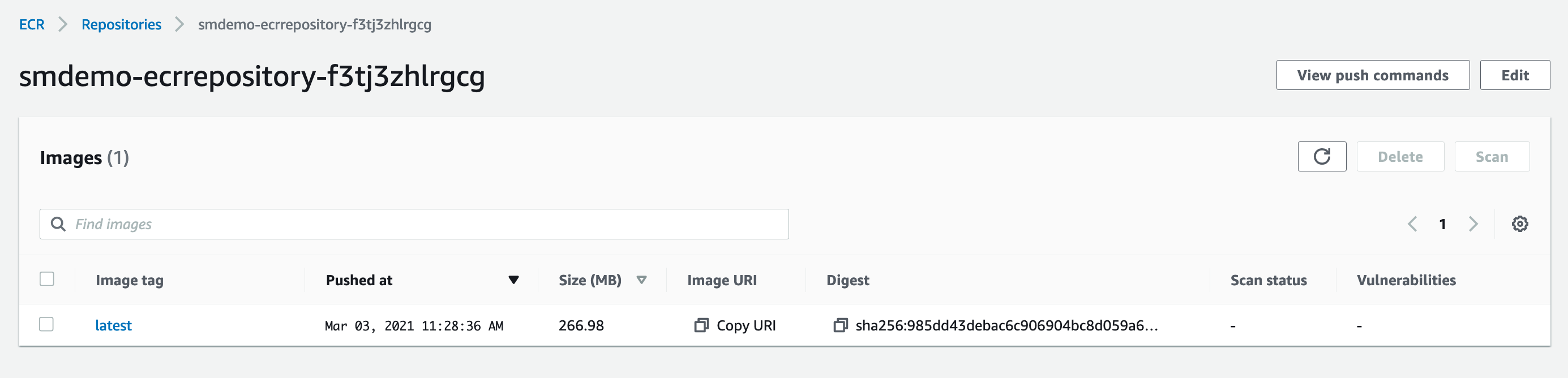
Once the process is complete, we proceed to configure AWS Fargate based on Amazon ECR.
Configure AWS Fargate
To configure AWS Fargate, we need to configure Task Definition first.
- Access the service Amazon ECS.
- In the left hand navigation bar, select Clusters.
- Click on the Cluster named with the following format
-ECSCluster-. - In the left hand navigation bar, select Task Definitions, select the Task named with the following format
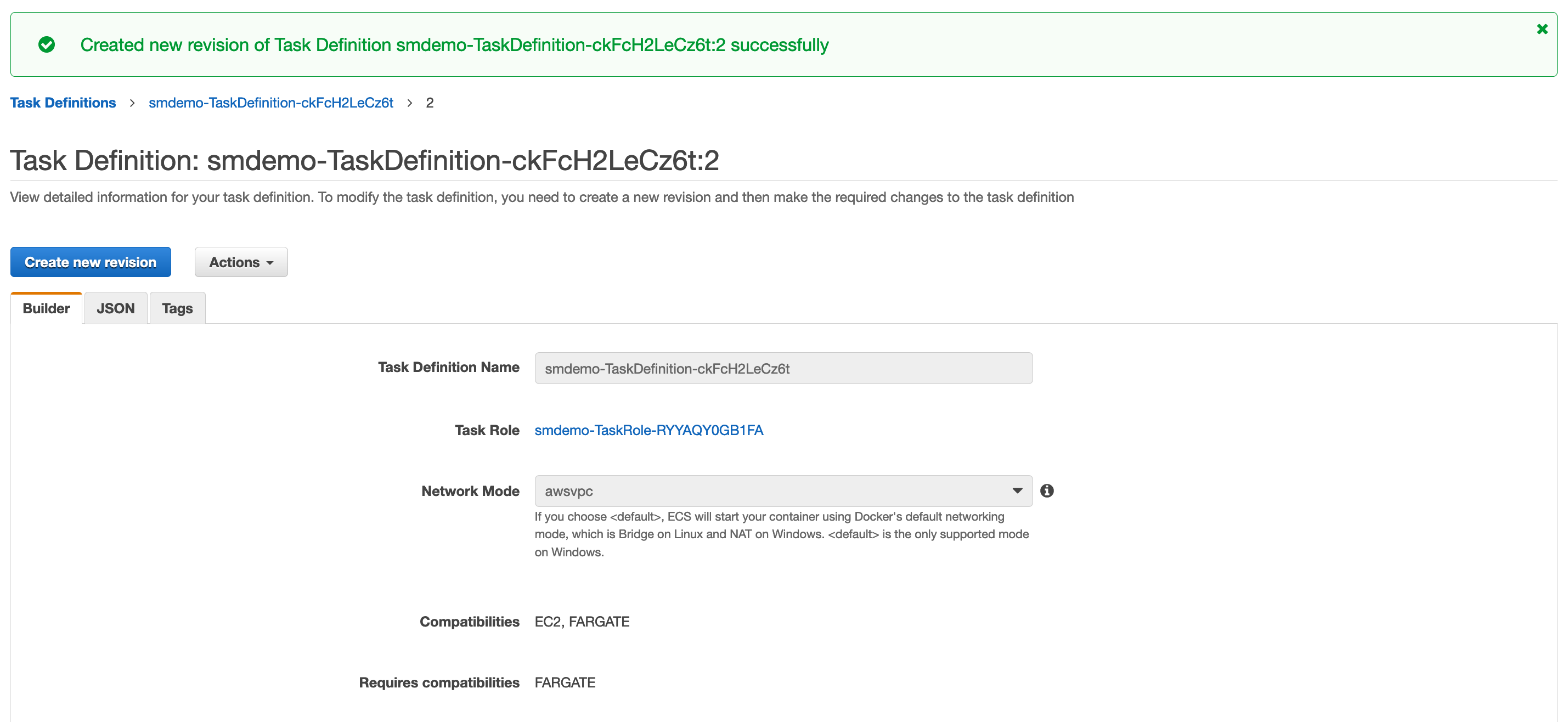
-TaskDefinition-. - Proceed to create a new revision, click the
Create new revisionbutton.
- Click the
Configure via JSONbutton.
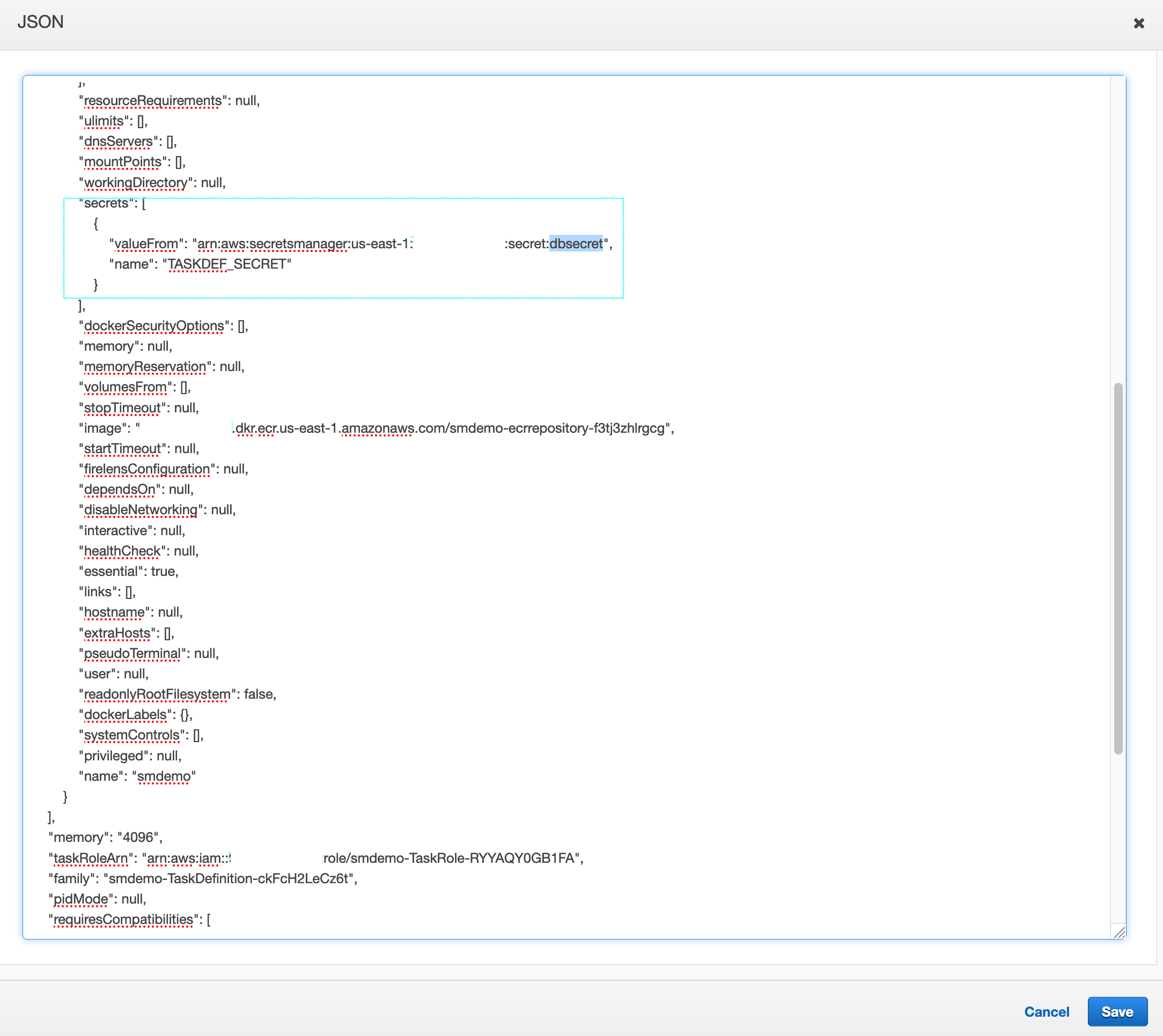
- Scroll to the secrets section, replacing
SECRETNAMEwith the Secret we created in the previous section.
- Press the
Savebutton. - Click the
Createbutton to proceed with initialization.
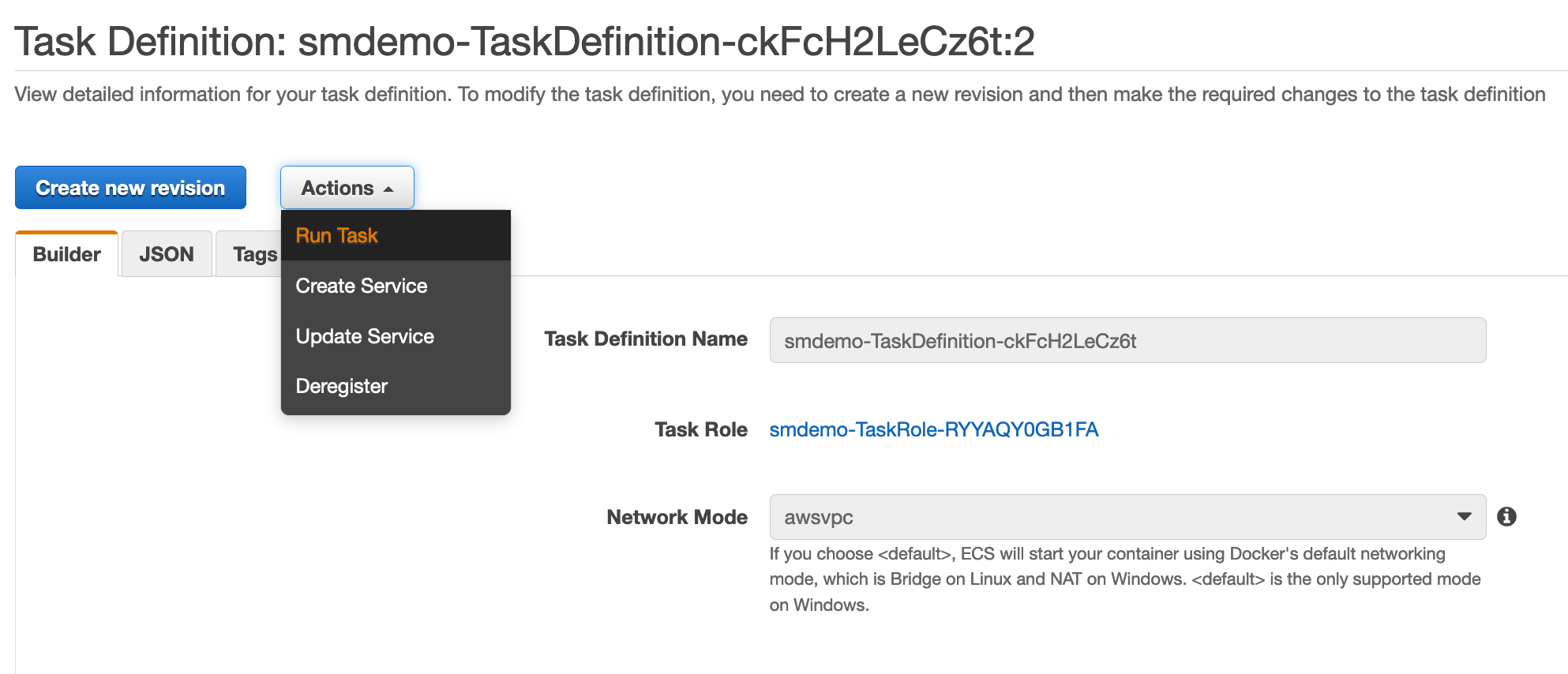
- Press the
Actionsbutton, selectRun Task.
- Proceed to select the following values:
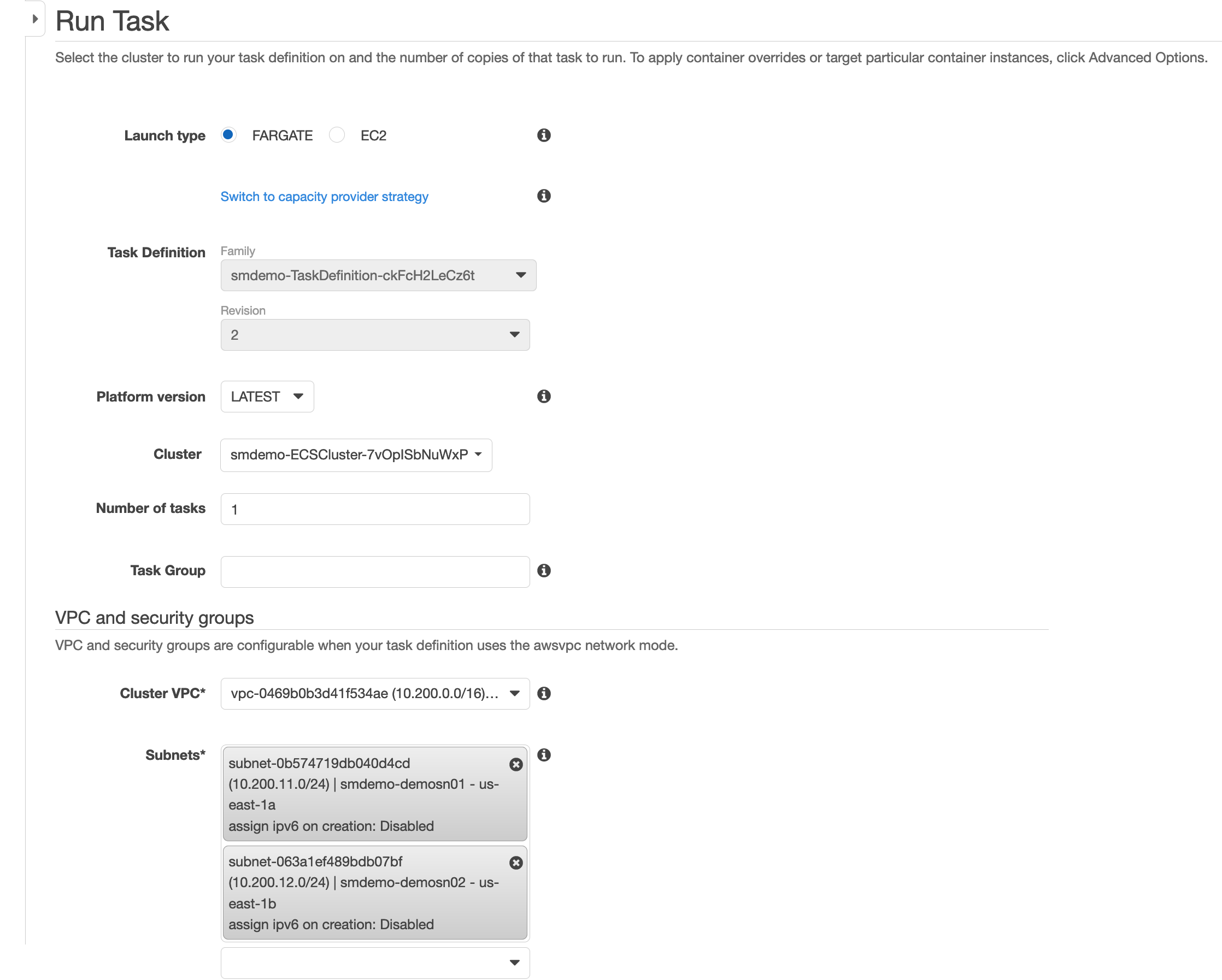
Launch Type: FargateCluster VPC: Select a prepared VPC with a CIDR of10.200.0.0/16.Subnets: Select all.Security Group: Select a name with the following format-BastionSG-.- Press the
Run Taskbutton. - Wait for the status from PROVISIONING, switch to PENDING and finally RUNNING.
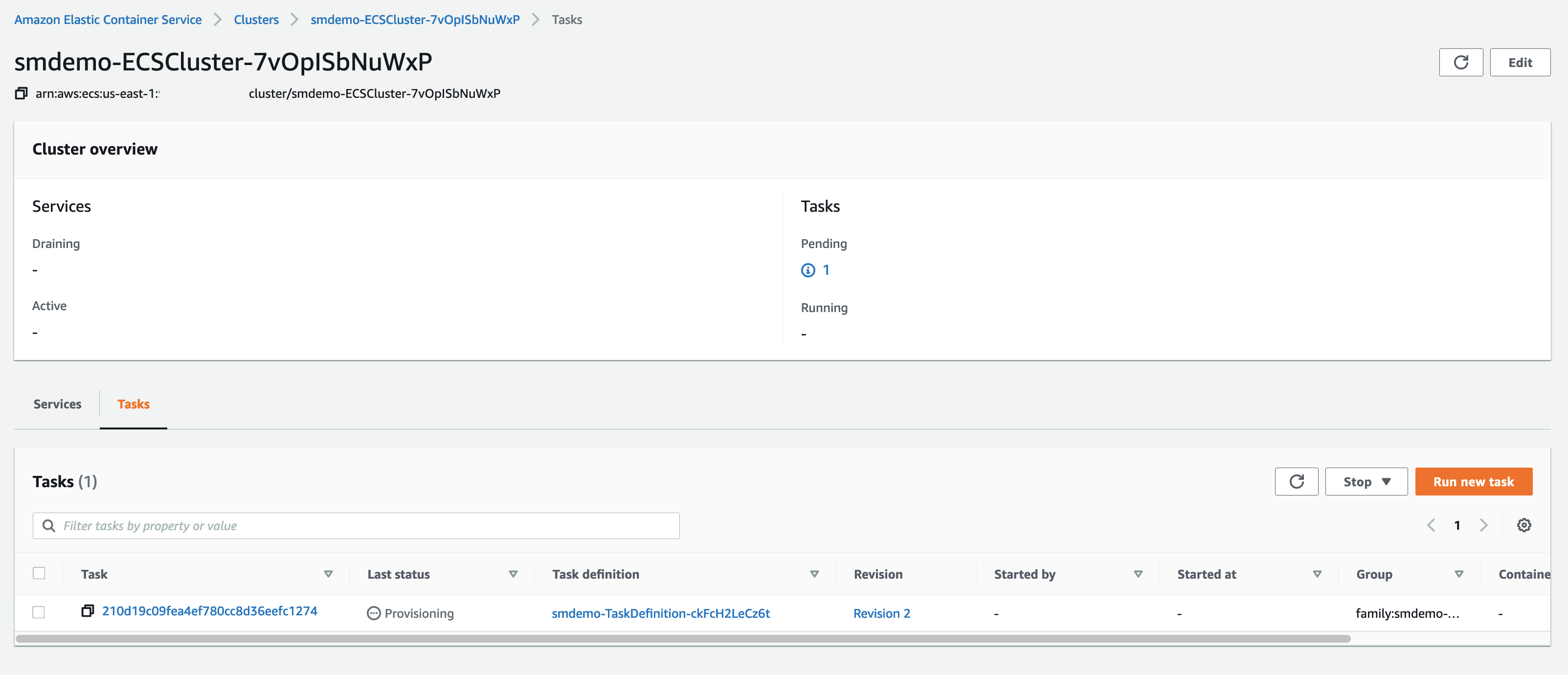
After the Tasks are in RUNNING state, we proceed to access the Fargate Container. First of all, we need to make a note of the IP address of a Fargate Container.
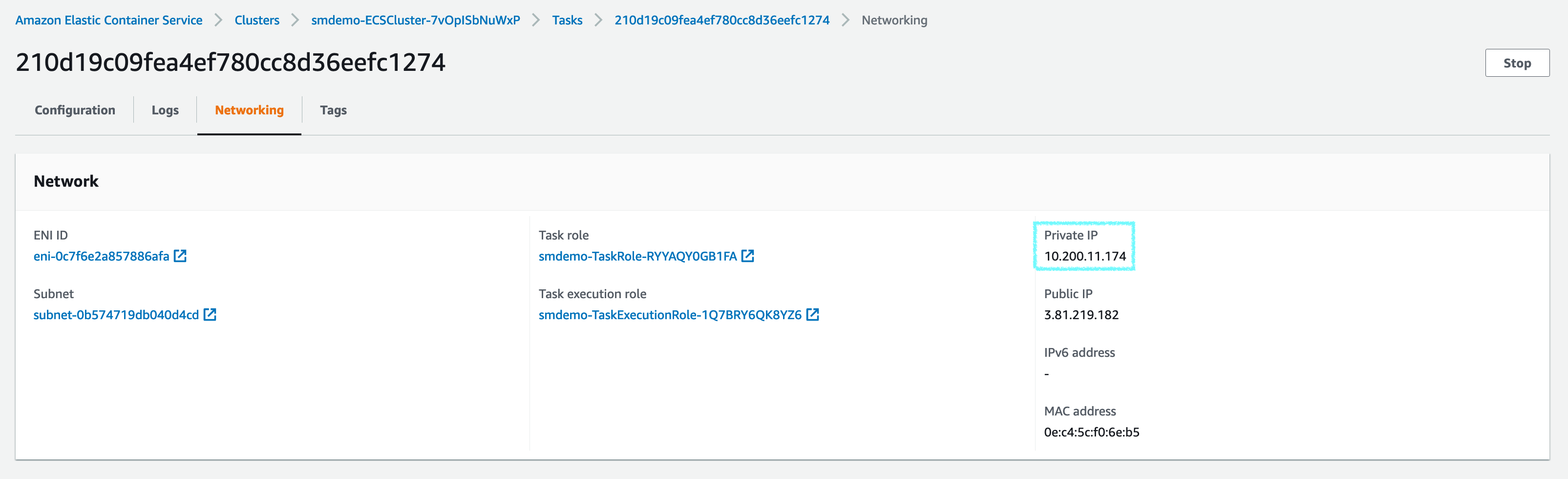
Access to Fargate Containers
From the Bastion Host, proceed to access the Fargate Container. When asked for a password, we use the value EC2UserPassword.
ssh <FARGATE_TASK_PRIVATE_IP>
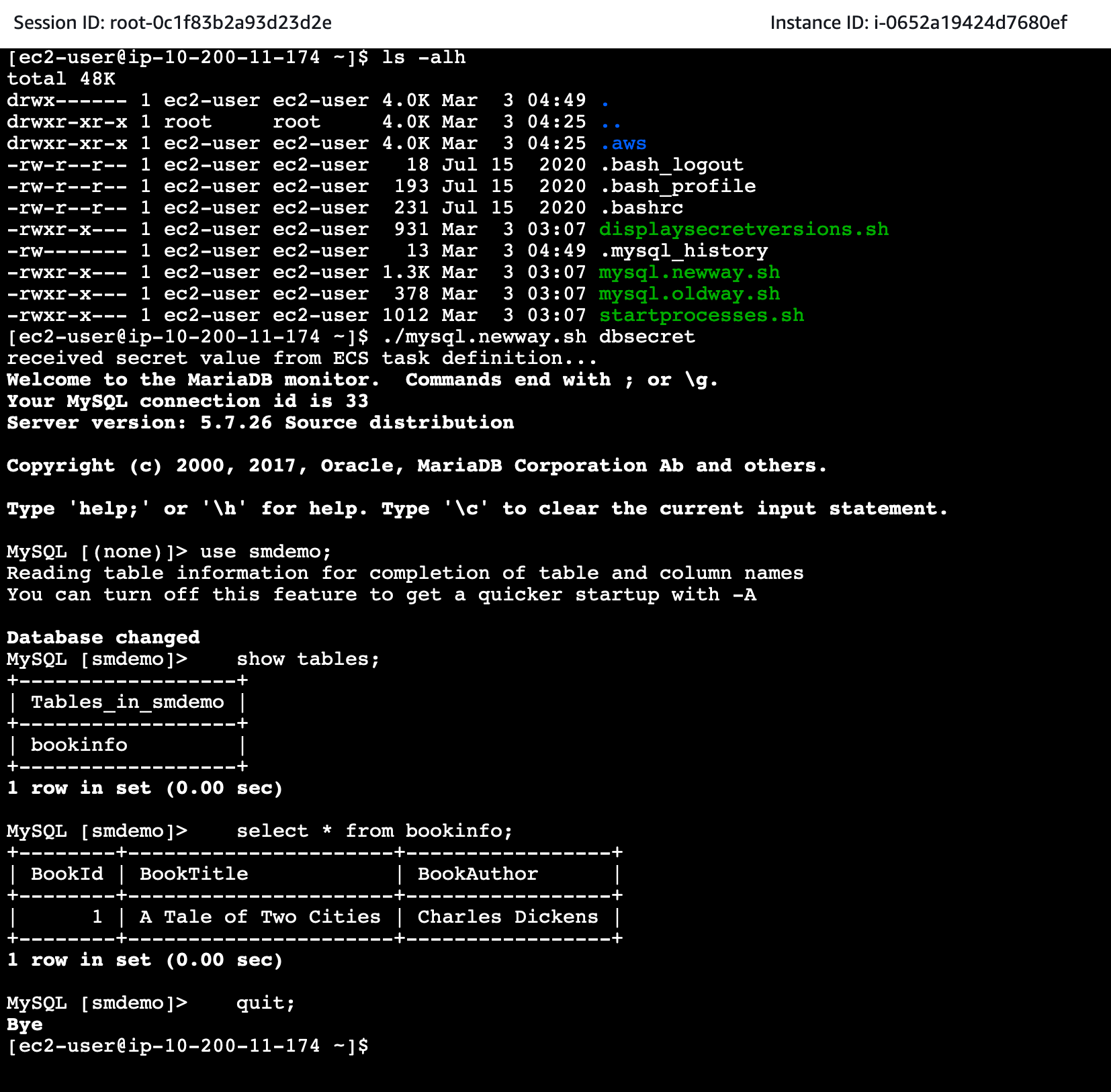
Access to RDS Database
In this part, we will use the new way through the shell script mysql.newway.sh.
- We execute
mysql.newway.shto access the RDS Database../mysql.newway.sh smdemo - Then execute SQL statements to check the existing data.
use smdemo; show tables; select * from bookinfo; quit; - The result will be similar to the following.
Conclusion and a better understanding of the process
After successfully accessing RDS Database from Fargate Container, we need to understand that there are many ways to access RDS Database, however, which option is secure and suitable for our application. we are the important thing.
For access from Bastion Host, we see the benefit of using shell script to access RDS Database, if we use the old hard-coded password method then after perform the Secret Rotation process, this method will not work.
For access from Fargate Container:
-
First, we use Secrets Manager ARN as
Environment Variablein Task Definition, then Fargate Containers can easily know and make access to *Secret * created earlier. -
On the Docker Image side, Dockerfile is used to enable the shell script
startprocesses.sh. This code will pass theEnvironment Variableparameters inside the Fargate Container. -
Fargate Containers can then use the value obtained from the
Environment VariableparameterTASKDEF_SECRETto perform access to RDS Database. -
The following is the code snippet for
startprocesses.sh.
touch /etc/profile.d/ecs.sh
chmod 644 /etc/profile.d/ecs.sh
env | \
grep "^TASKDEF_" | \
awk -F= '{printf "export %s=%c%s%c\n", $1, 39, $2, 39 }' \
>> /etc/profile.d/ecs.sh
- From the Task Definition, we can know the `Envionment Variables’ defined by the Fargate Container.
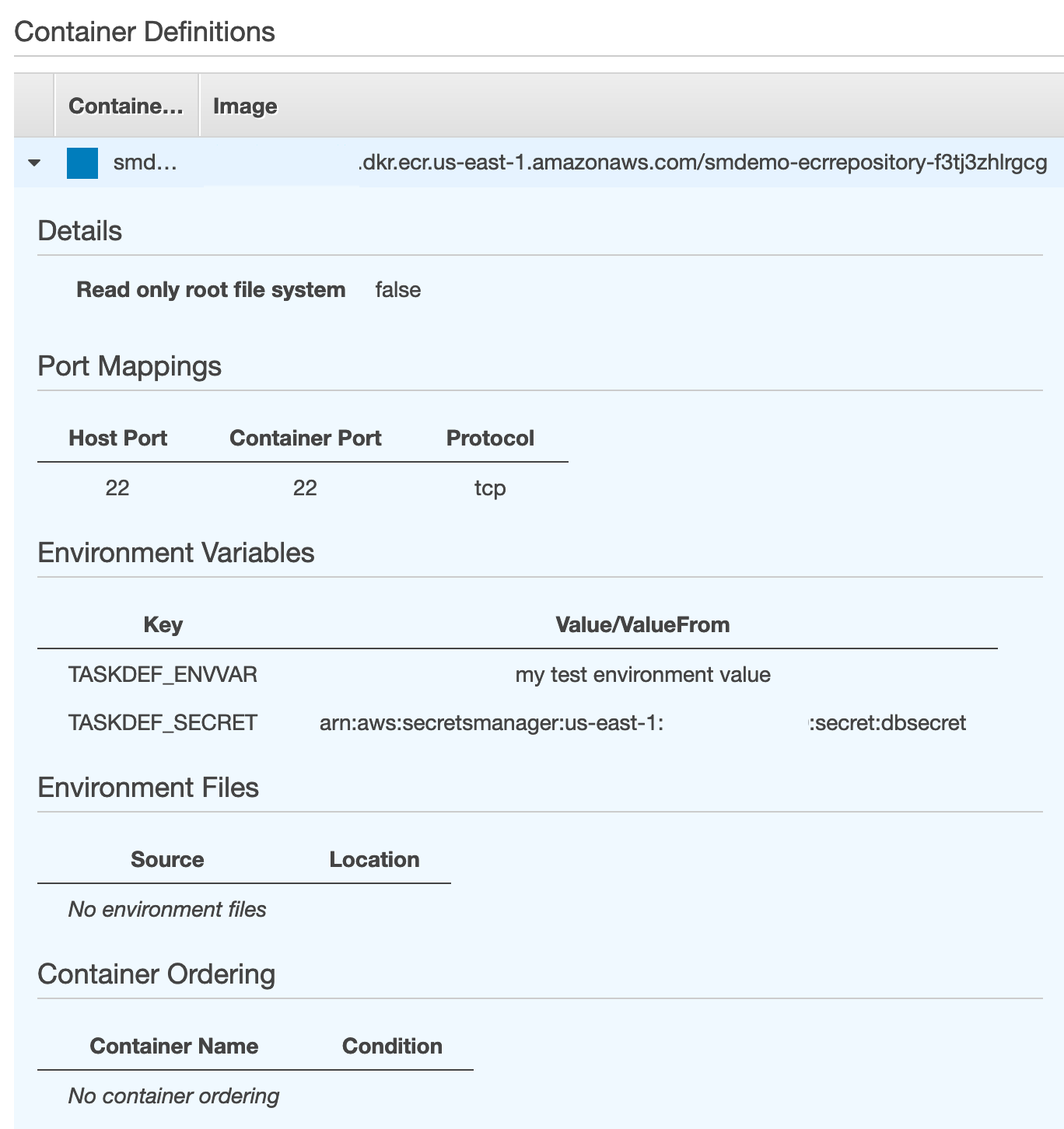
- From the Fargate Container, we can confirm the values of
Environment Variablewith the following command:
env|grep TASKDEF_SECRET
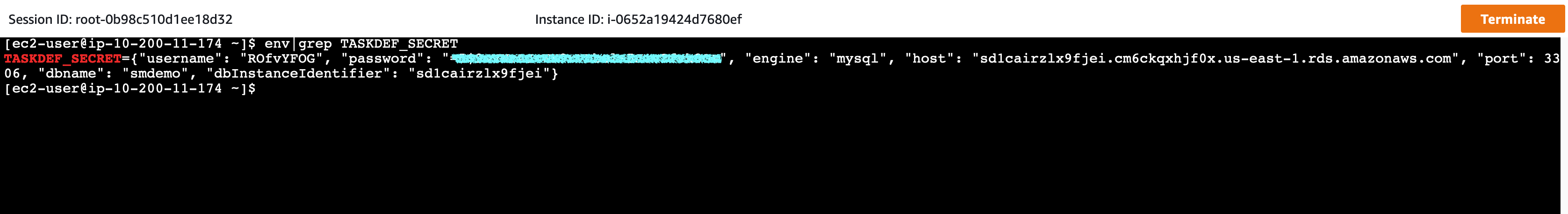
- The result will be in a format similar to this:
TASKDEF_SECRET={
"username": "<DBUser>",
"password": "<DBPassword>",
"engine": "mysql",
"host": "<RDS_ENDPOINT>",
"port": 3306,
"dbname": "<RDS_DATABASE>",
"dbInstanceIdentifier": "<RDS_ID>"
}