Using on RDS
Using Secrets Manager to interact with RDS
Overview
In this section, we will learn how to use the AWS Secrets Manager service to perform periodic password changes for the internal RDS Database.
Content
- Overview
- Secure RDS Credential with Secret Manager
- Access to RDS Database
- Secret Rotation
- Access RDS Database after completing Secret Rotation
Secure RDS Credential with Secret Manager
We will proceed to store RDS Credential values through the AWS Secret Manager service.
- Access the service Secrets Manager.
- Select
Store a new secret.
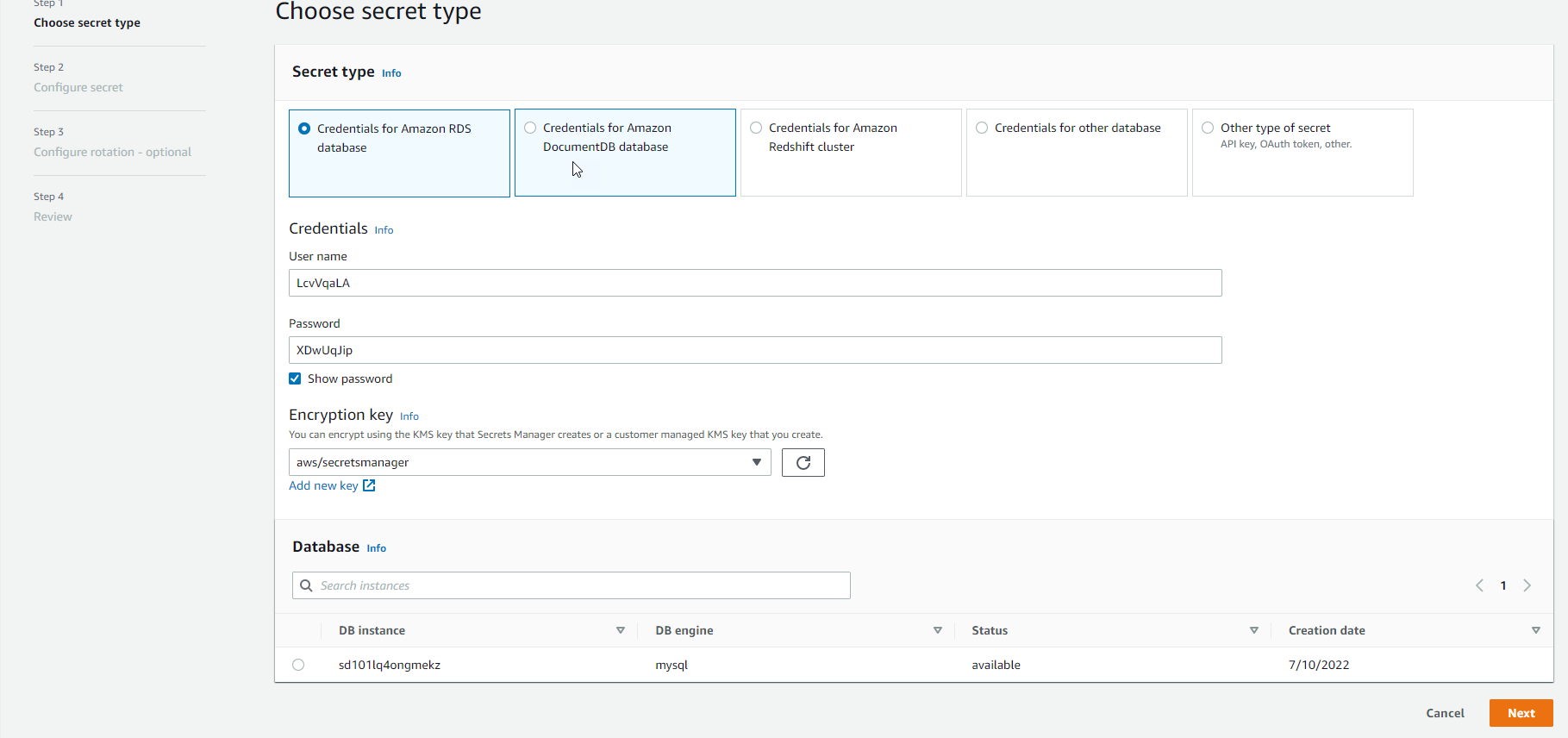
- In the Select secret type section, select the
Credentials for RDS databasebutton.- In the
Usernamebox: enter the value of DBUser. - In the
Passwordbox: enter the value of DBPassword. - In the
Select the encryption keybox, selectDefaultEncryptionKey.
- In the
- In the Select which RDS database this secret will access section, select the RDS instance corresponding to the value of DBInstance. Then, select the
Nextbutton. - In the Secret name and description field enter a name and description. Then, select the
Nextbutton.
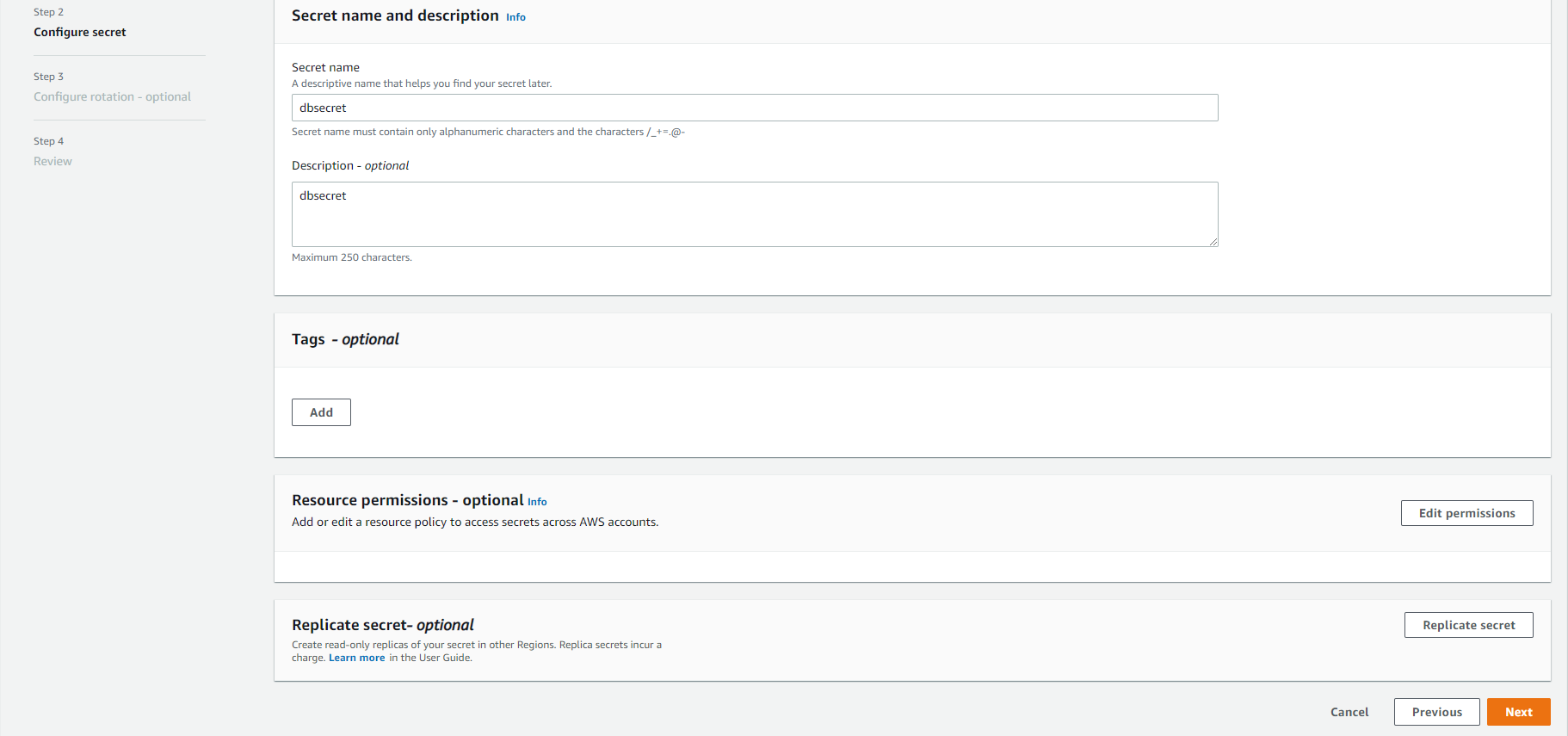
- In the Configure automatic rotation section, select the
Disable automatic rotationbutton. Then, select theNextbutton.
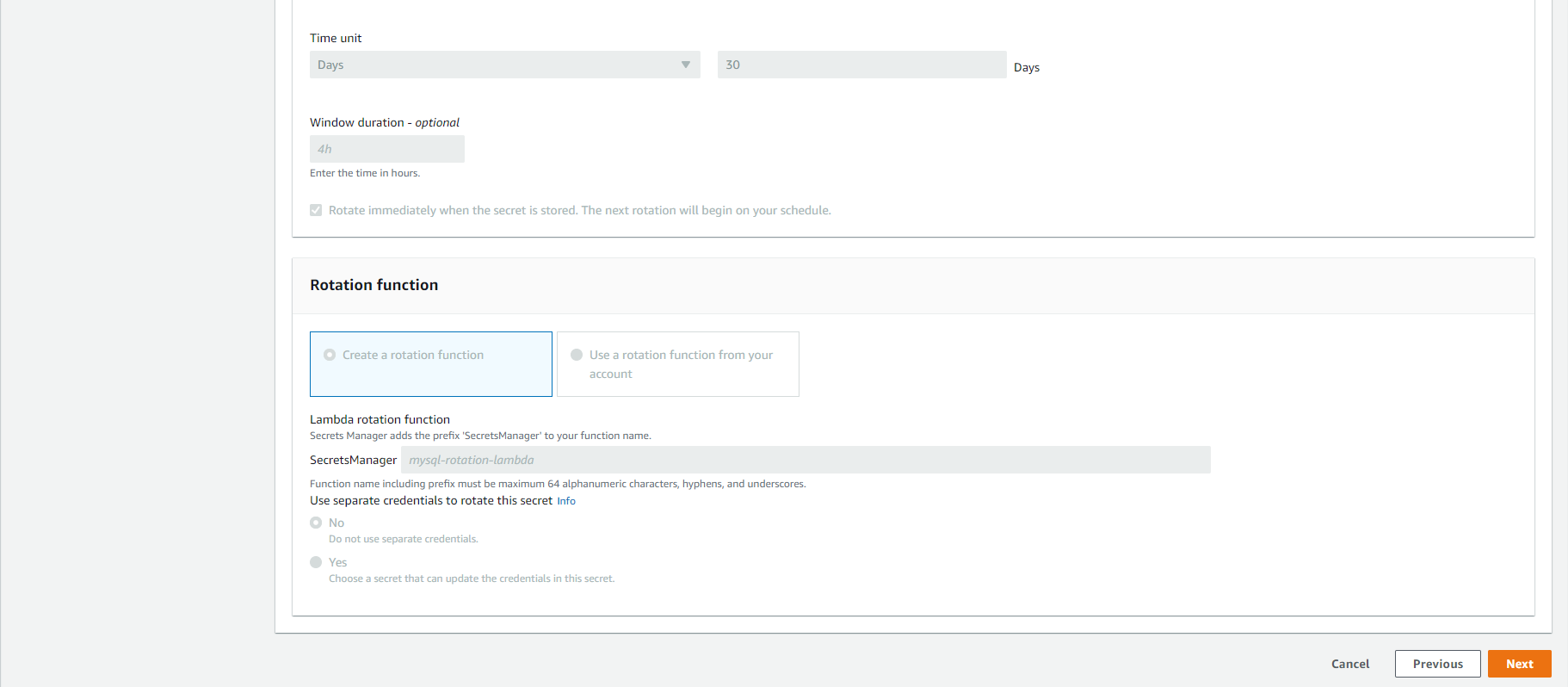
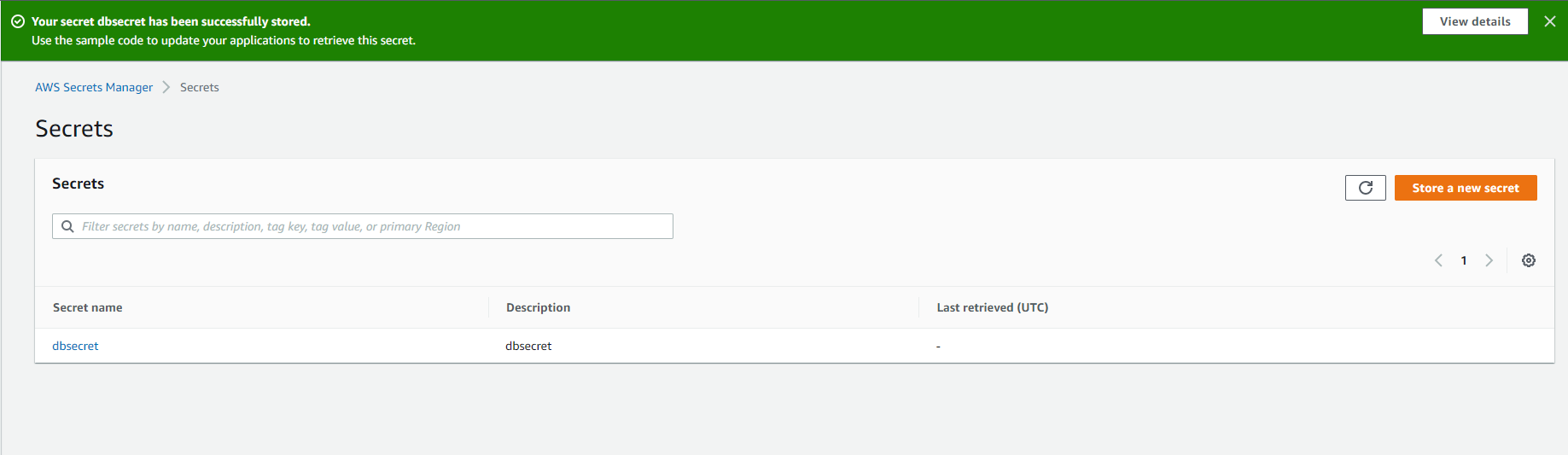
- In the Review section, select the
Storebutton.
With AWS SDK supporting multiple languages, we can easily integrate Secrets Manager with existing application, for example Java(https://docs.aws.amazon.com/code) -samples/latest/catalog/code-catalog-javav2-example_code-secretsmanager.html) or [Python](https://docs.aws.amazon.com/code-samples/latest/catalog/code-catalog-python- example_code-secretsmanager.html).
Access to RDS Database
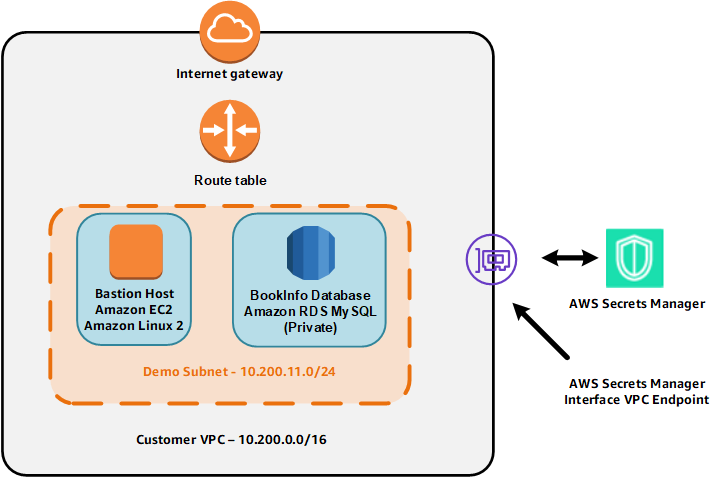
Now, we will use Bastion Host, which is allowed access to the RDS Database to execute the prepared shell scripts.
Access to Bastion Host with Session Manager
- Access the service Systems Manager
- In the left-hand navigation bar, select Session Manager.
- Press the
Start Sessionbutton. - Select the EC2 instance corresponding to the BastionIP value and press the
Start Sessionbutton.
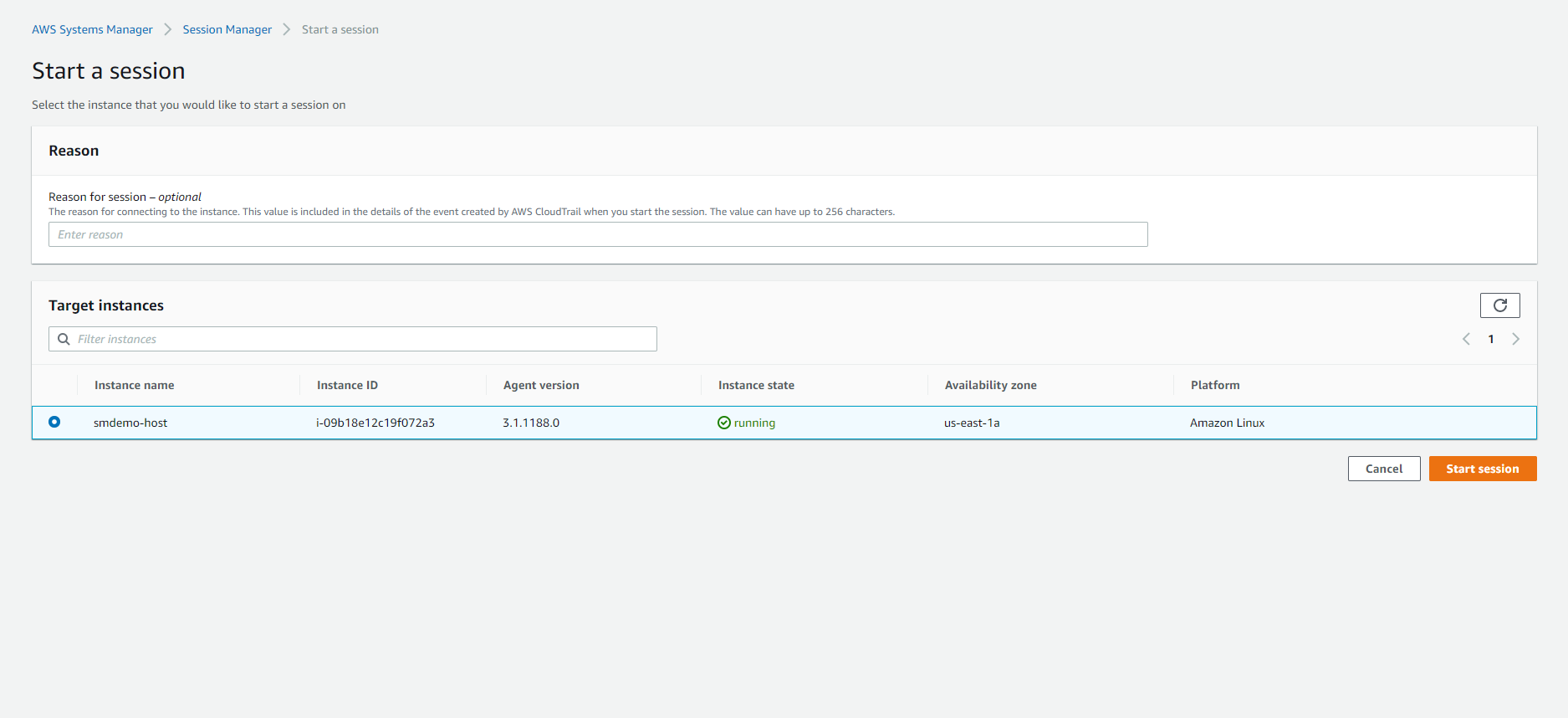
- In the new window bar, we will proceed to run the necessary commands.
Before running the scripts, we need to make sure the account used is ec2-user.
Proceed to switch to the ec2-user account with the following command:
sudo su - ec2-user
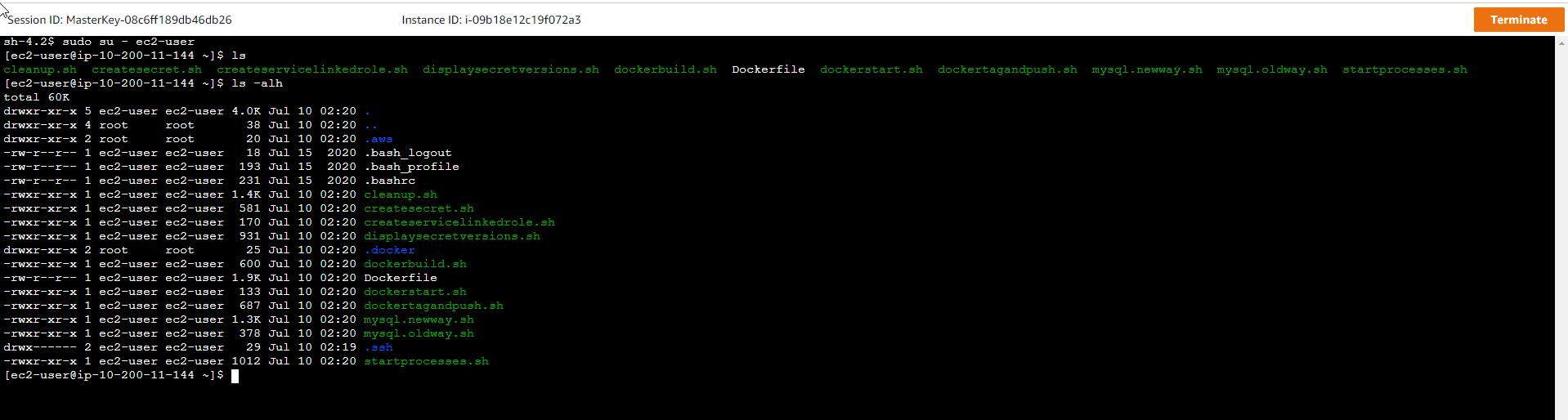
Execute Shell Scripts
- Search for prepared shell scripts.
- There will be 2 shell scripts prepared.
mysql.oldway.sh: this code is used to access the RDS database through the old way -hard-coded password.mysql.newway.sh: this code is used to access the RDS database through the new way -Secrets Manager.

For mysql.oldway.sh, the content inside the code will be similar to the following, where the following values will be pre-filled.
- PASSWORD
- USER
- ENDPOINT
#/bin/bash
# mysql.oldway.sh
# This is the old way of accessing a database, with a hard-coded password.
# This script will only work right after the CloudFormation template runs.
# After you store and rotate the secret, you will need to use the
# mysql.newway.sh script.
mysql\
-pPASSWORD\
-u USER \
-P 3306\
-h ENDPOINT
- We execute
mysql.oldway.shto access the RDS Database../mysql.oldway.sh

-
Then execute SQL statements to check the existing data.
use smdemo; show tables; select * from bookinfo; quit; -
The result will be similar to the following.
For mysql.newway.sh, the content inside the code will be similar to the following.
- The getsecretvalue() function is used to get the RDS Credential stored at the Secrets Manager service in the previous step, and then assign it to the argument
$1. - In turn assign the relevant values from the return results of the getsecretvalue() function.
- Make connection to RDS database via
mysqlcommand.
getsecretvalue() {
aws secretsmanager get-secret-value --secret-id $1 | \
jq .SecretString | \
jq fromjson
}
secret=`getsecretvalue $1`
user=$(echo $secret | jq -r .username)
password=$(echo $secret | jq -r .password)
endpoint=$(echo $secret | jq -r .host)
port=$(echo $secret | jq -r .port)
mysql\
-p$password \
-u $user \
-P $port \
-h $endpoint
The return value of the getsecretvalue() function is a JSON String.
The result will be similar to this:
{
"engine": "mysql",
"username": "myuser",
"password": "mypassword",
"host": "my-database-endpoint.us-east-1.rds.amazonaws.com",
"dbname": "myDatabase",
"port": "3306"
}
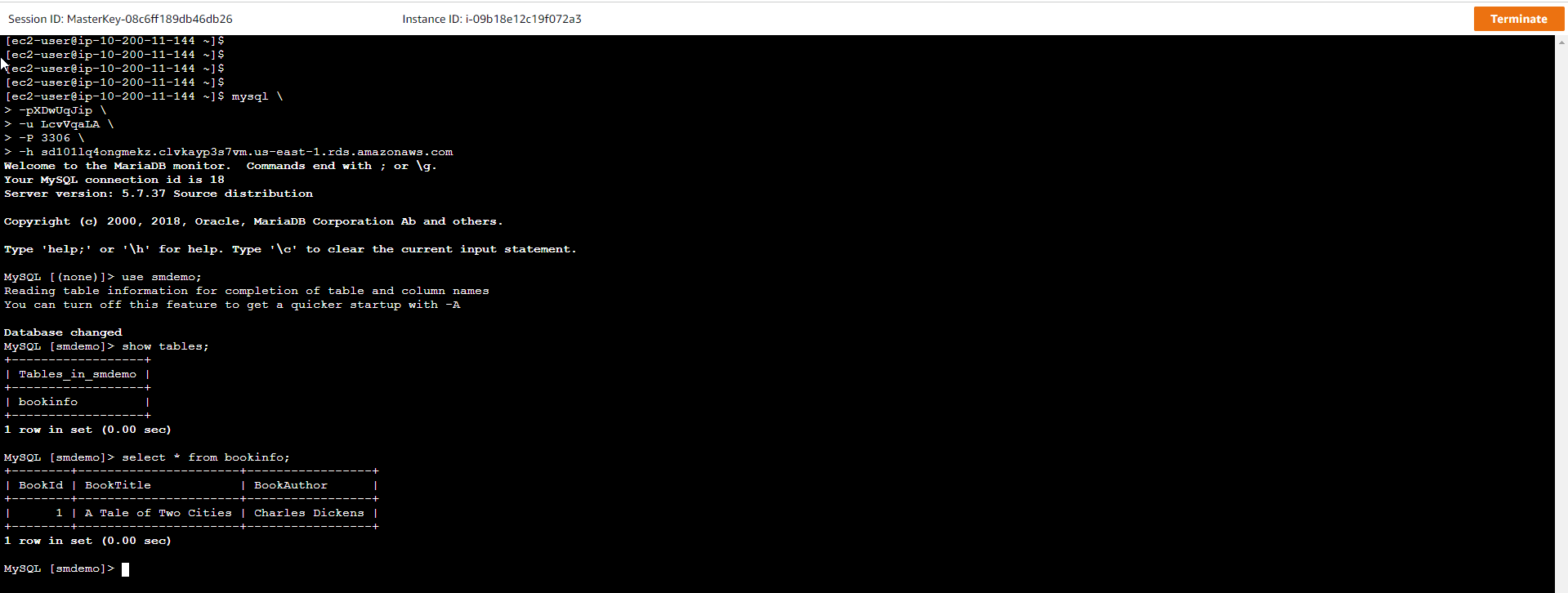
- We execute
mysql.newway.shto access the RDS Database../mysql.newway.sh <SECRET_NAME> - Then execute SQL statements to check the existing data.
use smdemo; show tables; select * from bookinfo; quit; - The result will be similar to the following.

Secret Rotation
After accessing the RDS Database through both ways, we will proceed with the Secret Rotation process. This is a periodic process to comply with security rules.
- Access the service Secrets Manager.
- Select the Secret that we created in the previous step.
- Click the
Edit rotationbutton.
- Select
Enable automatic rotation.
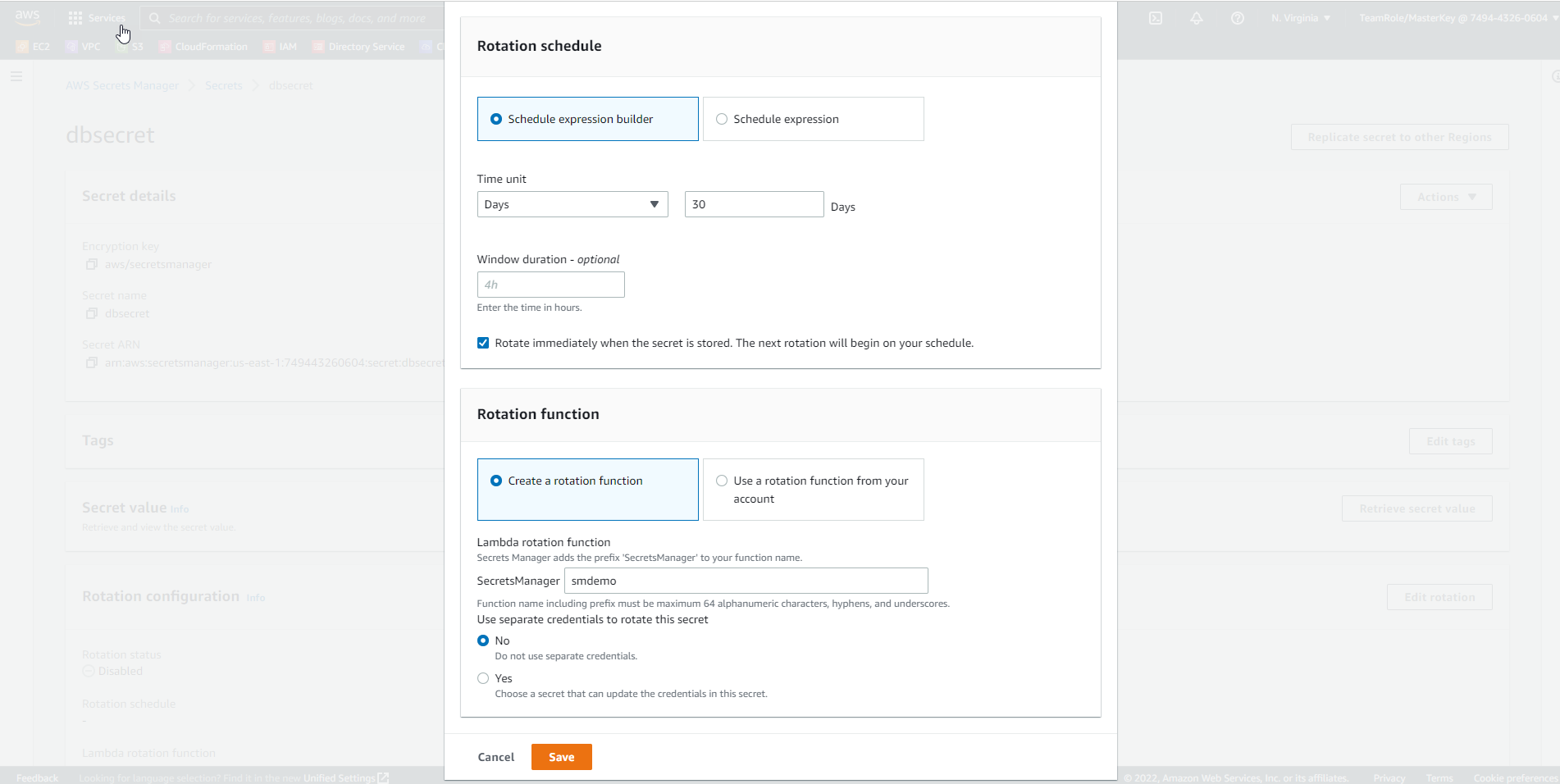
- In the Select rotation interval field, set the value to 30 days.
- In the New AWS Lambda function name field, enter the value smdemo.
- Under Select which secret will be used to perform the rotation, select
Use this secret. - Press the
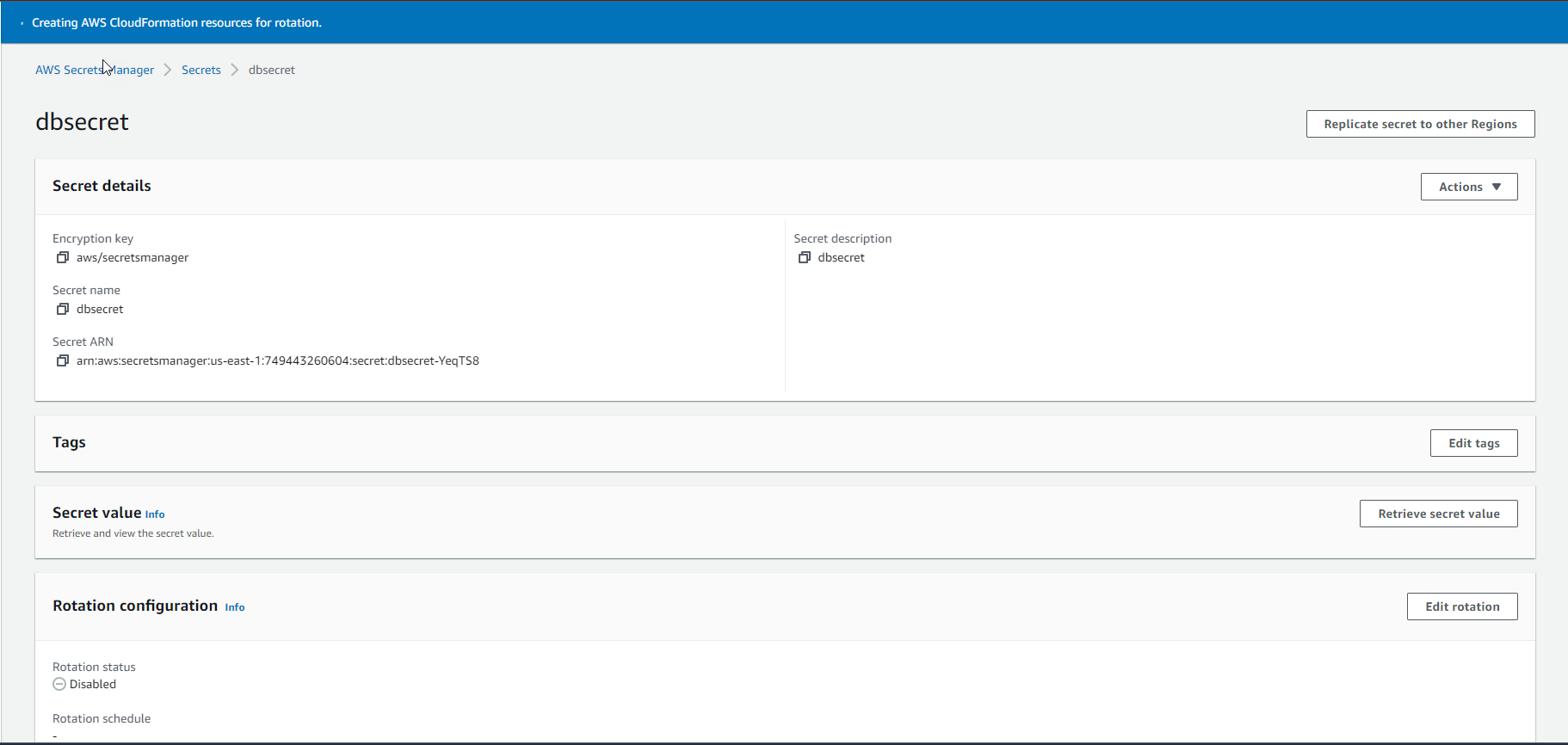
Savebutton. - There will be a message similar to this after Secret Rotation starts.
- When Secret Rotation is complete, the following message will appear.
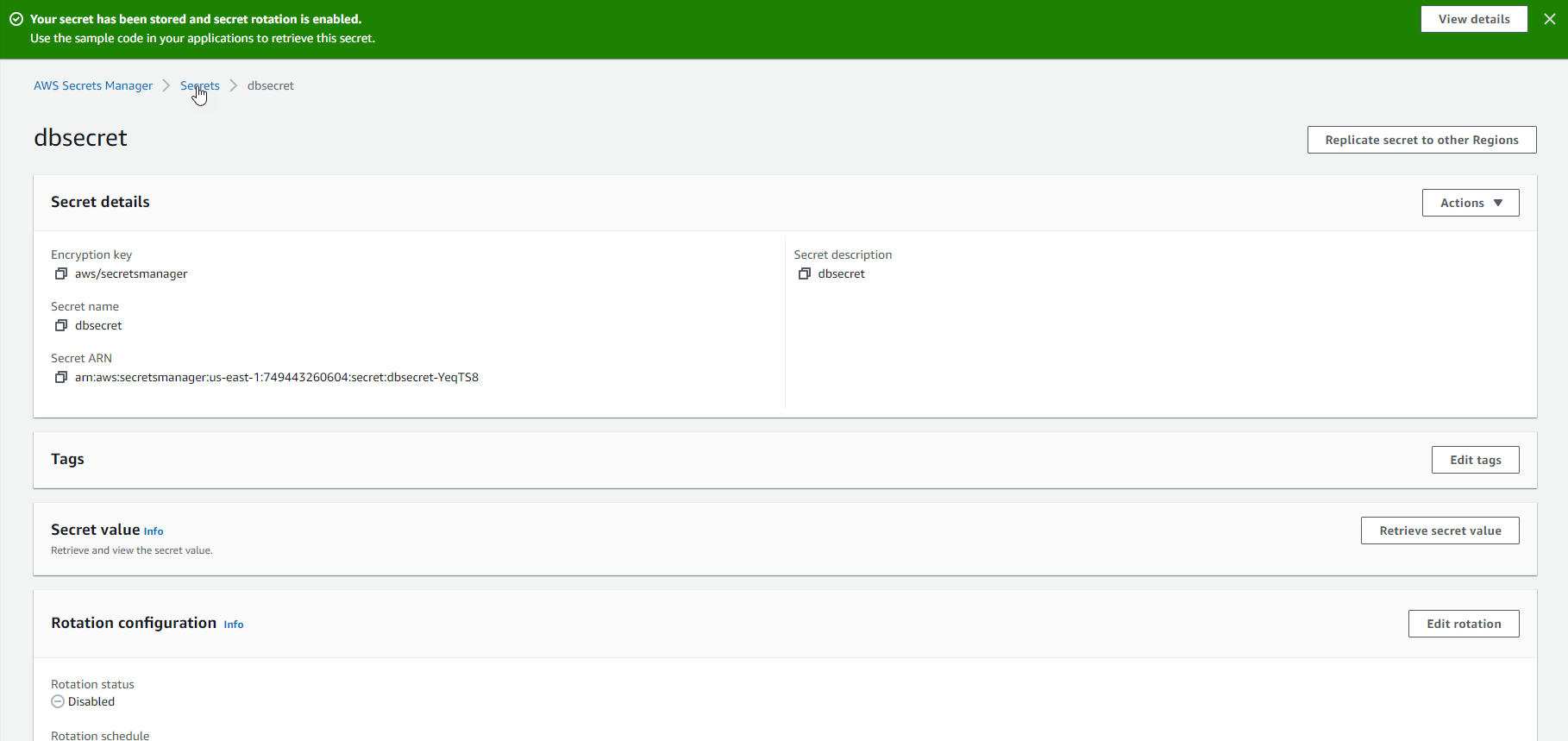
- To get the new value of Secret, press the
Retrieve secret valuebutton.
Secrets Manager will use AWS Severless Application Repository to install Lambda Function.
Access RDS Database after completing Secret Rotation
After completing the Key Rotation process, through the old and new access methods, we in turn access the RDS Database and observe the results.
For mysql.oldway.sh, the output will be as follows:

For mysql.newway.sh, the output will be as follows:

For the old way, because we used hard-coded password, when the password is changed, an error will appear and prevent access. For the new way, through Secrets Manager service, we can easily access RDS Database before and after Key Rotation process.